Search results for tag #GitHub
Oh, so while we here in Europe where focusing on #why2025 microsoft basically started sunsetting #GitHub as we knew it?
So Microsoft still doing EEE https://en.m.wikipedia.org/wiki/Embrace,_extend,_and_extinguish I guess...
Been watching the #GitHub posts scroll by all day, and it only occurs to me now to re-up this 2022 blog post about how I started self-hosting my #git repositories as part of my website using GitWeb: https://fietkau.blog/2022/moving_from_github
It's a pretty eccentric solution that's definitely less convenient than hopping to Codeberg (which would be my recommendation if your projects need modern collaboration tools), but maybe it'll speak to some of you. 😇
Just a periodic reminder that Forgejo, the software that powers the open-source GitHub alternative Codeberg, has been working towards implementing federation.
https://codeberg.org/forgejo-contrib/federation/
Might be worth contributing, if you have the time and skills!
We, the operators of this social media account, sometimes face dilemmas about what we want to post. For example: "Are you a Hubber and want to become a Berger? We're looking forward to you!"
Love it or hate it, one thing is certain: It doesn't really matter, because others are doing our marketing today. 🙃
and it occurs to me that I could/should move my personal website (https://kjordahl.net) off of GitHub pages as well, since it is just a static site. But another point of friction, and I'm not eager to do that work for little immediate return. But it is at least on my list to do so now.
I have just created a @Codeberg account and pushed my latest personal project there. Releases are still published from GitHub, but one step at a time.
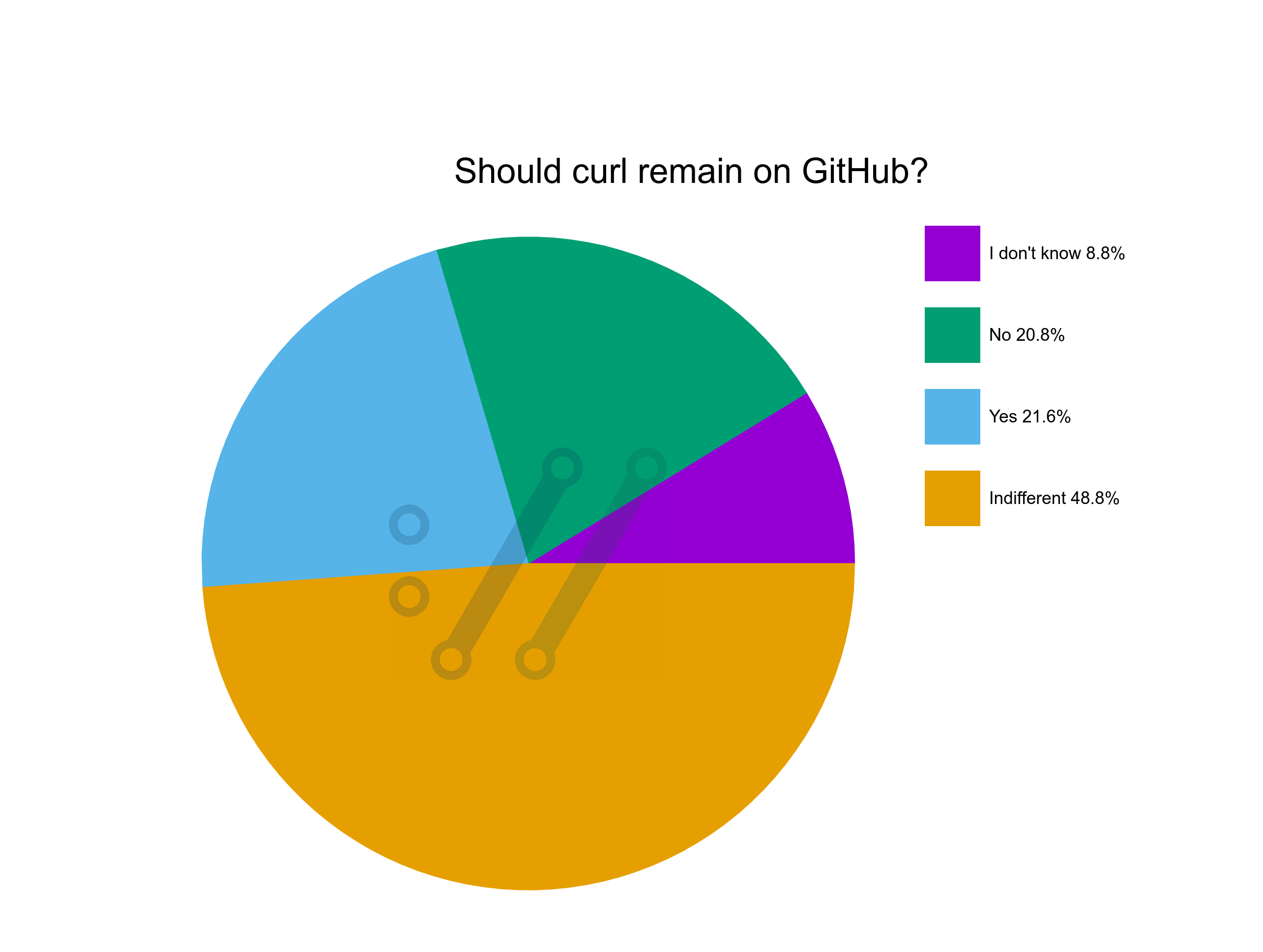
it is curious how many people feel they need to ask me why #curl is not moving off #GitHub
The cold and boring answer is money. GitHub sponsors us with a crapload of CI infra that there is no other company even close to doing.
So while they may be an AI-first delusional company, they help our project so much more than all other hosting sites combined.
It would be reckless and irresponsible of us to ignore this.
[New blog post]
GitHub to Codeberg Migration - Part 1 - Repositories
https://blog.sandra-parsick.de/2025/08/07/github-to-codeberg-migration-part-01/
People justify continuing to use #GitHub in all sorts of ways.
"OK, they're owned by Microsoft who has spent decades trying to crush FOSS, but..."
"Yes, they steal code to feed their planet-destroying LLMs, but..."
"Sure, they help ICE enforce fascist policy, but..."
"Yes, they're supporting genocide, but..."
There's no "but" clause that justifies supporting all of that.
Values require sacrifices. This is the price we pay for the world we want.
Don't collaborate. #Resist #GiveUpGitHub
it is curious how many people feel they need to ask me why #curl is not moving off #GitHub
The cold and boring answer is money. GitHub sponsors us with a crapload of CI infra that there is no other company even close to doing.
So while they may be an AI-first delusional company, they help our project so much more than all other hosting sites combined.
It would be reckless and irresponsible of us to ignore this.
Odd note added to the #GitHubActions cache repo:
https://github.com/actions/cache#note
"Thank you for your interest in this GitHub repo, however, right now we are not taking contributions.
"We continue to focus our resources on strategic areas that help our customers be successful while making developers' lives easier. While GitHub Actions remains a key part of this vision, we are allocating resources towards other areas of Actions and are not taking contributions to this repository at this time."
[New Blog Post]
Github To Codeberg Migration - Motivation
https://blog.sandra-parsick.de/2025/08/06/github-to-codeberg-migration-motivation/
GitHub CEO: Embrace AI or get out.
https://www.businessinsider.com/github-ceo-developers-embrace-ai-or-get-out-2025-8
PS. Here’s where to go: @Codeberg
(As an additional bonus, you’ll have the peace of mind of knowing you’re part of an anti-fascist not-for-profit cooperative instead of a trillion-dollar US corporation that’s helping Israel commit genocide.)
#git #sourceControl #revisionControl #GitHub #Codeberg #dev #AI #BigTech #Microsoft #israel #genocide #ethnicCleansing #apartheid #settlerColonialism #Palestine #StopIsrael #StopArmingIsrael #StopTheGenocide #FreePalestine
So I've just migrated all of my (admittedly entirely uninteresting) #GitHub repos to my own #Forgejo installation. I have no illusions that anyone will actually care about this move, but at least it removes one of the many pebbles in my stomach.
I did not need convincing that using and relying on centralised services run by large, non-European companies is bad; that has been clear for decades. Dependency, privacy concerns, legal implications and the general issue of "being the product" are all well-known and not-so-well-aged problems.
So what's new? Well that's easy: Most - or even all - the companies and services that fall under the umbrella loosely defined above have turned into outright Trump-apologists and bona fide supporters of fascism. Oh and they steal everyones stuff and feed it to their LLMs.
I should have done this a long time ago, and even so I'm keeping my presence on GitHub simply because it's pretty much a necessity to be able to contribute to other projects. And doing that is still more important than "sticking it to the guy": The positive impact of contributing (and maintaining a low bar for me to do so) still seems too important to outright deleting me account.
I'm willing to hear arguments to the contrary, though. #SelfHosting #Independence #EU #DigitalFreedom #OnlineFreedom
Since Microsoft is organising a European Sovereign Tech Fund, we should ask Lockheed Martin to put together a European Sovereign Defense Fund. There’s probably also opportunity here to bring Amazon in to advise on EU labour standards and have McDonald’s take the lead on food safety policy in the EU.
#EU #USA #corporateCapture #europeanSovereignTechFund #microsoft #github #openSource #freeSoftware #tech #freedom #humanRights #democracy
The only way Microsoft should be involved in a European Sovereign Tech Fund is if we fund it by taxing the living shit out of them.
But having them organise and influence it (and who gets funded by it), thereby de facto giving Microsoft EU taxpayer subsidies? Get the fuck out of here.
There are no words to describe how angry this attempt at corporate capture gets me when we’ve been working on sovereign tech in the EU for the past seven years with zero EU funding (not for lack of trying).
Note which people and organisations allow their names to be used to legitimise this effort so you don’t trust a thing they say on this subject in the future.
https://github.blog/open-source/maintainers/we-need-a-european-sovereign-tech-fund/
#EU #FOSS #freedom #tech #funding #EuropeanSovereignTechFund #corporateCapture #openWashing #BigTech #microsoft #GitHub
I'm surprised that running scheduled #GitHub jobs for particular branches seems to require YAML kung-fu from hell. Is that not one of the most fundamental features of a CI system? on > push > branches works. on > schedule > branches doesn't? Why?
Dew Drop Weekly Newsletter #439 - Week Ending July 4, 2025. zc.vg/fxPq8?m=0 #dewdrop #newsletter #aspnetcore #javascript #azure #xaml #windev #csharp #dotnet #ai #agile #devops #github #IoT #podcasts #m365 #sqlserver
Dew Drop Weekly Newsletter #439 - Week Ending July 4, 2025.
#dewdrop #newsletter #aspnetcore #javascript #azure #xaml #windev #csharp #dotnet #ai #agile #devops #github #IoT #podcasts #m365 #sqlserver

![[?]](https://pleroma.anduin.net/media/e42775318fd38a77b2c02300192e27e61861443424849feef9767918512fac8b.png?name=blob.png)