Search results for tag #OpenSource
Do you Patch machines regularly? Even when your bandwidth is constrained take the time to patch them and be safe.
In this example I photographed the patching of one of the micro SD Cards of the SBC.
I've patched all of them.
For the X86 machines the Os on the main 2280 SSD is patched. Other SSD and HDD will follow. The BSD HDDs need patch Love 💕 too. They will get it
#Raspberry #Pi5 #SBC #technology #ARM #X86 #patching #Linux #OpenSource #BSD #freeBSD #ghostBSD #programming
I think that there isn't an existing off-the-shelf model.
The idea of separating "good" commercial copying and re-use from "bad" commercial copying and re-use has long done the rounds in free software circles, and it has always come up against two things:
1. How does one define "good" and "bad"?
1. Such distinctions are against the principles, held by many of the founders of these ideas, that freedom is for everyone.
https://gnu.org/philosophy/free-sw.html#selling
https://opensource.org/osd#persons-or-groups
There's almost certainly an on-going debate about excluding large (language) models from "free to copy and use" rights. But it's just another case in a long-standing argument about trying to exclude various "bad" categories of users; and the people on the prevailing side, when coming up with "free" and "open", have long rejected this.
So you're not going to find something from CC or GNU or some such that you can just pull off the shelf for achieving such an end.
The last new #Linux #kernel for 2025 was just released and there are some really cool changes all around. One of the new additions is detection for FreeBSD's #bhyve #hypervisor. Wicked cool!
From the article:
"In what might be a sign of the quiet continued spread of FreeBSD, the kernel can now detect and handle that it is running under FreeBSD's built-in bhyve hypervisor. Coincidentally, FreeBSD 15.0 just appeared as well, and in this release bhyve supports over 255 virtual processors [PDF] in a VM. Now Linux can handle that configuration."
The juicy details are here:
And just like that, we’ve hit 50% of our goal for the end of the year! 🎉
Have you joined #FriendsOfGNOME yet? If not, this is your sign to join 750 other amazing supporters:
If so, help us keep up the momentum by sharing with your friends, especially those outside of the typical contributor community. Let’s end the year strong!
#FriendsOfGNOME #GNOME #GNOMEFoundation #OpenSource #FOSS #Linux
FreeBSD 15.0 Now Available
The FreeBSD Project has announced the availability of FreeBSD 15.0-RELEASE, introducing updated toolchains, enhanced hardware support, improved security features, and key updates across the base system. This release continues the Project’s focus on stability, long-term maintainability, and consistent engineering.
We encourage you to review the release notes and upgrade guidance
Read the full announcement: https://www.freebsd.org/releases/15.0R/announce/
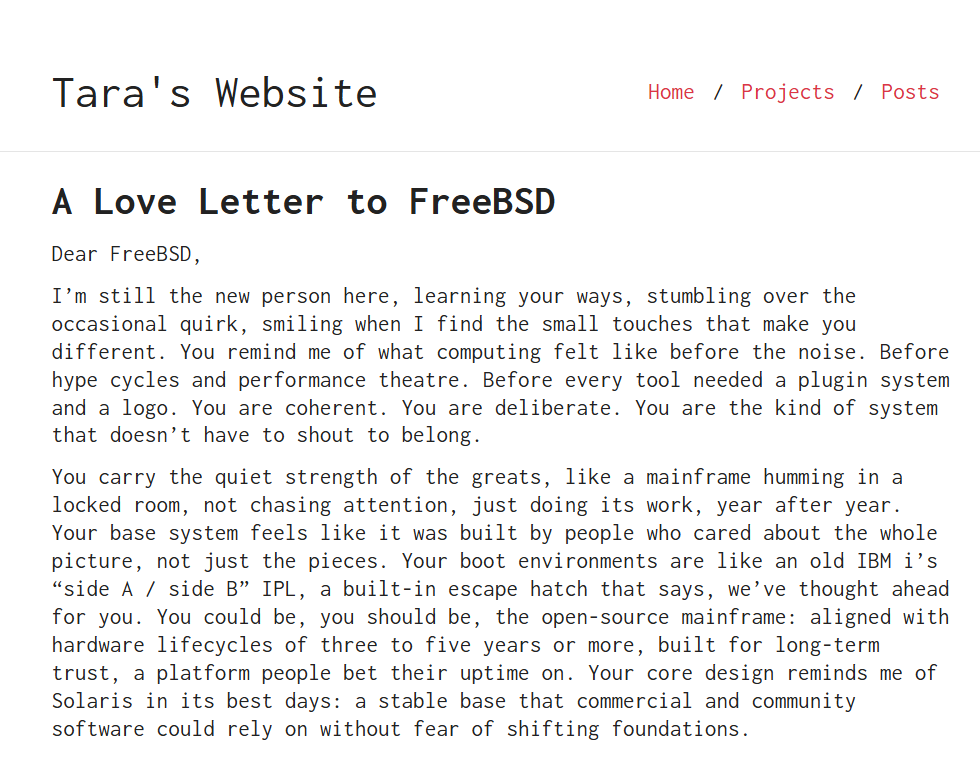
Thank you for sharing this, Tara.
Your post reflects several qualities that continue to define FreeBSD, including clarity, stability, and long-term design. It’s valuable to hear how newer contributors experience the Project.
Read the full letter: https://lnkd.in/dtcQebh2
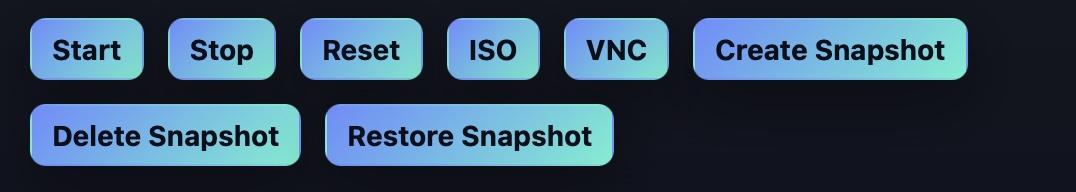
Ever messed up an update? We got you covered! Simply restore your Snapshot!
You can now also manage (create, delete, restore) a snapshot of your Box! If you ever messed up your application, OS update or anything else - simply go back to your last snapshot and try again! This way, you can test and learn #BSD even better and easier!
cc: @gyptazy
#education #opensource #FreeBSD #OpenBSD #NetBSD #RUNBSD #learning #ipv6 #freevm #freevps #community #fosdem #hosting #selfhosting #snapshot
We are launching an end-of-year fundraising campaign with a simple goal: to reach 1,500 Friends of GNOME. And we need your help!
https://blogs.gnome.org/foundation/2025/12/01/join-friends-of-gnome/
This week, we will also be sharing and celebrating the accomplishments of GNOME over the past year here on the fediverse; be sure to follow #FriendsOfGNOME!
Finally, if you’re already a Friend of GNOME or join this month, please join us in posting with #FriendsOfGNOME as well so that we can thank you. 😊
Cutting entry-level roles in the AI era is a "profound strategic error."
The LF’s Chief Economist @Frank_Nagle explains in a new @FortuneMagazine article why sacrificing junior talent jeopardizes future leadership and institutional knowledge.
Read the full piece: https://fortune.com/2025/11/19/why-its-a-mistake-to-cut-entry-level-jobs-ai-mit-scientist/
#AI #FutureOfWork #OpenSource
What Brings People to FreeBSD?
Recent comments on our community post showed just how diverse the paths into FreeBSD can be. Some users have been running FreeBSD since the 1990s for its stability and predictable behavior. Others found it through TrueNAS, books, mentors, user groups, or simply curiosity.
Thank you to everyone who shared their experience. These stories help newcomers see the many ways FreeBSD supports real-world work.
#BoxyBSD chat is now also available in #irc!
People asked for old school possibilities to take part on the BoxyBSD chat and here we go! Finally, you can also simply join #BoxyBSD on Libera (next to your #FreeBSD channels)! This bridge was written by @gyptazy to support additional chat communications.
Important: This IRC channel is bridged between #Discord and #Matrix to have a unified communications flow without splitting the community. If you don't like Discord, please don't join this channel!
Infos about how to connect by IRC to Libera IRC:
- https://libera.chat/guides/connect
#FreeBSD #OpenBSD #NetBSD #DragonflyBSD #MidnightBSD #OpenSolaris #Debian #FreeVPS #VPS #FreeVM #VirtualMachines #OpenSource #BSD #RUNBSD
How do you prefer to describe software?
#FreeSoftware #OpenSource #FOSS #FLOSS
| Free Software: | 0 |
| Open Source Software: | 0 |
| Free Open Source Software (FOSS): | 0 |
| Free/Libre Open Source Software (FLOSS): | 0 |
| Something else (comment): | 1 |
After nearly 10 years, Mastodon founder Eugen Rochko steps down as CEO, transferring assets and the trademark to a non-profit ⚖️
The move aims to protect Mastodon’s decentralized, user-controlled values while reducing founder stress and ensuring sustainable governance 🌐
🔗 https://itsfoss.com/news/mastodon-ceo-steps-down/
#TechNews #OpenSource #Decentralization #SocialMedia #Privacy #UserControl #FOSS #DigitalRights #Community #Governance #Software #Innovation #TechPolicy #CyberSecurity #Sustainability #Mastodon
GNOME has had that system for more than two decades or so IIRC {if I recall correctly} they're 27 ATM.
I had seen it in the first couple of years of GNOME spawn and development, when the programmers chose the route of less configuration & more dictation
#sh #GNOME #reg #editor #OpenSource #programming #Linux #UI #Xorg #POSIX
Btw for the Engineering / Computer Science / Physics students on the #Fediverse, you can still apply to the CERN Summer Student Program 2026! CERN does a lot of cool #opensource things too.
Stuck on a specific configuration for a jail? Our community is a great resource! Don't hesitate to reach out on our forums or chat channels. Let's solve it together.


 🍵
🍵  boosted
boosted🦀 APT Rust requirement raises questions // @lwn
「 Julian Andres Klode's declaration that APT would require Rust in May 2026 means that a few of Debian's unofficial ports must either acquire a working Rust toolchain or depend on an old version of APT. This has raised several questions within the project, particularly about the ability of a single maintainer to make changes that have widespread impact 」
Petition: Anerkennung von Open-Source-Arbeit als Ehrenamt in Deutschland
#petition #opensource #digitaleresilienz #anerkennung #ehrenamt
Forget the chaotic Black Friday sales! 🤯 NetBSD 🚩 offers the BEST deal: it's 100% FREE! Always has been, always will be. Perfect for self-hosters and anyone seeking pure, open-source goodness without spending a dime. No catches, just solid OS. #NetBSD #BlackFriday #FreeSoftware #SelfHost #RetroComputing #OpenSource #Linux #RunBSD
Happy Disability Pride Month everybody :)
During the past few weeks, there's been an overwhelming amount of progress with accessibility on GNOME Calendar:
• Event widgets/popovers will convey to screen readers that they are toggle buttons. They will also convey of their states (whether they're pressed or not) and that they have a popover. (See !587)
• Calendar rows will convey to screen readers that they are check boxes, along with their states (whether they're checked or not). Additionally, they will no longer require a second press of a tab to get to the next row; one tab will be sufficient. (See !588)
• Month and year spin buttons are now capable of being interacted with using arrow up/down buttons. They will also convey to screen readers that they are spin buttons, along with their properties (current, minimum, and maximum values). The month spin button will also wrap, where going back a month from January will jump to December, and going to the next month from December will jump to January. (See !603)
• Events in the agenda view will convey to screen readers of their respective titles and descriptions. (See !606)
Accessibility on Calendar has progressed to the point where I believe it's safe to say that, as of GNOME 49, Calendar will be usable exclusively with a keyboard, without significant usability friction!
There's still a lot of work to be done in regards to screen readers, for example conveying time appropriately and event descriptions. But really, just 6 months ago, we went from having absolutely no idea where to even begin with accessibility in Calendar — which has been an ongoing issue for literally a decade — to having something workable exclusively with a keyboard and screen reader! :3
Huge thanks to @nekohayo for coordinating the accessibility initiative, especially with keeping the accessibility meta issue updated; Georges Stavracas for single-handedly maintaining GNOME Calendar and reviewing all my merge requests; and @tyrylu for sharing feedback in regards to usability.
All my work so far has been unpaid and voluntary; hundreds of hours were put into developing and testing all the accessibility-related merge requests. I would really appreciate if you could spare a little bit of money to support my work, thank you 🩷
• https://ko-fi.com/theevilskeleton
• https://github.com/sponsors/TheEvilSkeleton
(Boost appreciated)
#Accessibility #a11y #DisabilityPrideMonth #GNOME #GNOMECalendar #GTK #GTK4 #Libadwaita #FreeSoftware #FOSS #OpenSource
After two weeks of writing, revising, and trying to make everything as digestible as possible, I finally published "GNOME Calendar: A New Era of Accessibility Achieved in 90 Days", where I explain in detail the steps we took to turn GNOME Calendar from an app that was literally unusable with a keyboard and screen reader to an app that is (finally) accessible to keyboard and screen reader users as of GNOME 49!
https://tesk.page/2025/07/25/gnome-calendar-a-new-era-of-accessibility-achieved-in-90-days/
#GNOMECalendar #GNOME #Accessibility #a11y #DisabilityPrideMonth #Linux #FOSS #OSS #OpenSource #FreeSoftware #GTK #libadwaita
Salvatore Sanfilippo (creator of Redis, and more) published a beautiful video inspired by my latest blog post. I was really pleased! It's in Italian, but auto-generated English audio track is available.
I've had such a fabulous time at the TYPO3Con over the last two days. Lots of great conversations with agencies who are increasingly finding they're being asked to provide marketing stack services and delighted to find @mautic as an open source alternative to the many proprietary tools out there. Almost lost my voice from all the talking!
Can't wait for the next day, and the awards event tomorrow .. even got my posh frock dusted down!


 🍵
🍵  boosted
boosted Blender 5.0 Released with a UI Overhaul, Smarter Nodes, and HDR Support // @linuxiac
Blender 5.0 Released with a UI Overhaul, Smarter Nodes, and HDR Support // @linuxiac
https://linuxiac.com/blender-5-0-released-with-a-ui-overhaul-smarter-nodes-and-hdr-support/





![[?]](https://gts.korora.social/fileserver/01EBRSX3YN3BMANV473WFZERFR/attachment/original/01JT3C6FRJCMXH2QBWC45C58DK.jpeg)

