Search results for tag #NetBSD
I love #NetBSD. I love working on its code base, and I love running it. I burned out on computers in the teens--especially with a lot of the places that Linux has gone--and playing more with NetBSD has brought back that spark of joy.
Anyway, the foundation's fundraiser is coming up short right now, if you have extra, it's great community and plucky little OS.
https://mail-index.netbsd.org/netbsd-users/2025/10/26/msg033327.html
🌟 Introducing BSD.cafe 🌟
Excited to present the first building block of the BSD Cafe project! When I registered this domain months ago, I envisioned a themed bar where we can casually chat about *BSD systems, Linux, and Open-Source technology among friends, acquaintances, and patrons. But like any bar, discussions can cover a wide range of topics while respecting everyone.
BSD.cafe will be a hub for various tools and services, powered by *BSD.
The first brick is a new Mastodon instance, a gateway to the Fediverse. Registration is open, and the server will be moderated under clear guidelines promoting good behavior and zero tolerance for hate towards anyone. Inclusivity, respect, and constructive dialogue are the key values of this new instance.
The main server is currently hosted in Finland on a small VM, based on #FreeBSD. Services are divided into VNET jails, connected in a LAN via a local bridge. A VPN system is also present and have been able to move individual jails to different, more powerful, machines.
Multimedia data and cache are hosted on another physical server (FreeBSD, within a jail), with Cloudflare in front. The aim is to cache and geodistribute data, reducing network traffic on the main VPS.
Reverse proxy (frontend), mail server, media server, and the instance itself are reachable via #ipv6.
The instance started empty. No unnecessary content was pre-loaded; I want it to grow organically based on users' interests and following. There won't be any preemptive blocks at this stage. Users are encouraged to promptly report anything they find worth flagging.
Join us at https://mastodon.bsd.cafe to build a constructive and inclusive community—a safe and relaxing space for everyone.
Our wiki, located at https://wiki.bsd.cafe, features essential links and articles related to the BSD world. It provides an overview of the tools, services, rules, uptime, and more information about the BSD Cafe Services.
A Matrix server, a Miniflux RSS Reader, the Wiki itself, and the BlendIT Lemmy instance are all part of the BSD Cafe services, with more to come.
#BSD #OpenSource #Fediverse #Community #Tech #Networking #Mastodon #Inclusivity #FreeBSD #NetBSD #OpenBSD #DragonflyBSD #Linux #OSS #SysAdmin #Miniflux #RSS #Matrix
@lymenzies
Well, depending on how far you get with run - here's a nice little thing - OrangePi Zero, #netbsd starts up, but the network card doesn't work 😉
Hehe, I left #netbsd installing on my #vax (a lowly #MicroVAX 3100/30, with 32MB RAM and 25MHz CPU) over the weekend. It's running on the network now, but is *spectacularly* slow, even on NetBSD 7.2 😂
It takes about 80 minutes to boot, and 2-3 minutes to login on a serial console.
It's effectively unusable, but was an interesting #retrocomputing exercise to get up and running. Ah well, back to #VMS.
Latest 𝗩𝗮𝗹𝘂𝗮𝗯𝗹𝗲 𝗡𝗲𝘄𝘀 - 𝟮𝟬𝟮𝟱/𝟭𝟬/𝟮𝟳 (Valuable News - 2025/10/27) available.
https://vermaden.wordpress.com/2025/10/27/valuable-news-2025-10-27/
Past releases: https://vermaden.wordpress.com/news/
#verblog #vernews #news #bsd #freebsd #openbsd #netbsd #linux #unix #zfs #opnsense #ghostbsd #solaris #vermadenday
Latest 𝗩𝗮𝗹𝘂𝗮𝗯𝗹𝗲 𝗡𝗲𝘄𝘀 - 𝟮𝟬𝟮𝟱/𝟭𝟬/𝟮𝟳 (Valuable News - 2025/10/27) available.
https://vermaden.wordpress.com/2025/10/27/valuable-news-2025-10-27/
Past releases: https://vermaden.wordpress.com/news/
#verblog #vernews #news #bsd #freebsd #openbsd #netbsd #linux #unix #zfs #opnsense #ghostbsd #solaris #vermadenday
This week for the #OverUnder series, my guest is @bt!
He gave his thoughts about #Openwrt, #NetBSD, #Qutebrowser, #Braindumps, and #FrozenYogurts!
He also recommendended two #books
#mastodon #fediverse #blogs #blogging #bookstodon #BSD #OpenBSD
https://lazybea.rs/ovr-039
 boosted
boostedMade some improvements in Wii graphics support on #NetBSD recently. Instead of doing RGB to YUY2 conversion in software (very slow!) I managed to work out how to make the GX to do it for me. This has a nice side effect in that it actually reproduces colours more accurately than my hacky software solution.
Ce soir, restriction budgétaire sur les espaces disques ! #virtualisation avec #NetBSD et #NVMM, tout de suite sur https://twitch.tv/ahp_nils ! #sysadmin #devops #twitchfr #twitchstreamer #TwitchStreamers #BSD #qemu
Let's Help NetBSD Cross the Finish Line Before 2025 Ends https://lobste.rs/s/wbymah #netbsd
https://mail-index.netbsd.org/netbsd-users/2025/10/26/msg033327.html
Let's Help NetBSD Cross the Finish Line Before 2025 Ends
https://mail-index.netbsd.org/netbsd-users/2025/10/26/msg033327.html
hotuser script from the OpenDTrace toolkit.Another issue is that the only way to stop dtrace is to kill -9 it, which takes the watched process with it in the fall..
Halp? :)
 boosted
boostedWant to reduce e-waste? The NetBSD🚩 Project keeps old hardware alive, turning it into firewalls or retro-gaming machines.
To keep this work going (and fund new RISC-V & WiFi renewal!), the @netbsd needs our help to hit its 2025 goal before the year ends.
Please donate today: https://www.netbsd.org/donations/
#WhyIRunNetBSD #NetBSD #OpenSource #RISCV #Sustainability #Ewaste #RetroGaming #Linux
Finally!
I'm happy to announce the R1OS Forum, a place for everyone interested in free and open source software that wants to discuss about it, get help using it, or simply want to be part of a new community.
https://r1os.com/sites/blog/forum-platform-launched.php
Forum: https://forum.r1os.com
#r1os #linux #freebsd #openbsd #netbsd #illumos #opensource #freesoftware
Pretty interesting how an old hardware works well and compute well in the strange configurations.
Prereqs: Intel Atom N2800 1866 MHz and 2 Gb RAM.
Since there are no NetBSD builds of xray-core and v2raya — I spin up a FreeBSD VM inside the Qemu and without NVMM accelerator (not supported by my CPU). Execute these programs inside this VM — and the server still running and even doesn't overload 
 boosted
boostedTinkering with #NetBSD on this ex-Sophos box has been way more fun than I expected. No more bad web UIs, no proprietary crap, just a basic npf.conf file I can access over SSH or a serial console. Done!
I can't wait for our access point to arrive, then I can finally retire our ancient home network kit.
... [SENSITIVE CONTENT]
Hi! Let's make an #introduction !
I'm your average computer engineer that has absolute no idea of what to do.
My only talent in computer science is to pretend that I know and keep trying until it works.
I use #arch btw. But currently teaching myself #NetBSD.
I though it would be a good idea to join an instance where people talk about BSDs and share the fun. Fun like me getting to break something.
At least, is not something productive...
So, it has been like three months using FIDO/U2F keys instead of passwords. Both in my NetBSD and Arch systems.
I use a "medium" quality password to decrypt the filesystems and other one to decrypt the password manager. And that's it.
No password to log-in, to unlock screen, to run doas/sudo, etc. Just this little penguin and press its button.
Also, I'm using this as 2FA for all websites that support it. Lemmy doesn't. It's the only place where I don't use it, yet.
Because U2F uses the domain name, this is a strong protection against phishing. A similar domain may trick my eyes, but not the key.
I'm very bad at memorizing passwords, and worse at typing them. Unlocking the screen without typing my password like 3 times is a bless.
The problems: if my laptop is decrypted anybody with this penguin is root. It's kinda my Horcrux. Also, I need a second one stored safely as a backup.
So I officially have two horcruxes. Destroy both and I can't log-in anywhere.
#fido #u2f #infosec #NetBSD #arch #keepass #password #horcrux
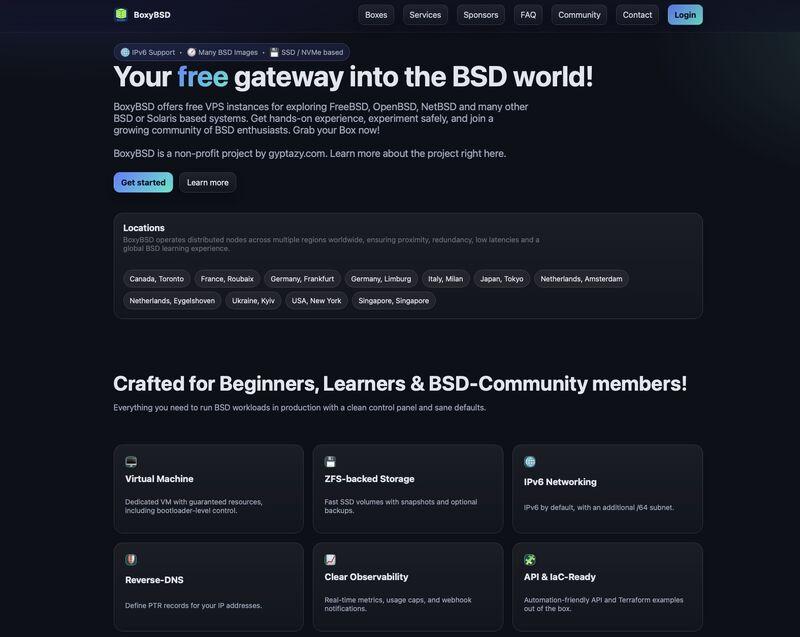
We at @BoxyBSD are happy to announce our new and modern website!
While the missions keeps the same by providing a free place for beginners to learn, educate themselves and test things in the wild on BSD-based systems (such like #FreeBSD, #NetBSD, #OpenBSD (or even #smolbsd) and many more ones) with public accessible IP addresses, the old nerdy design only hit a niche of users.
We want to make BoxyBSD more accessible & enjoyable to everyone and this is one of the first steps. We know, a laggy SSH connection doesn't make fun and therefore, we're also setting up new locations to provide you a better latency independent of your location.
During this time, signups for new users are currently deactivated until the new locations are up and running and the first real-user tests within the new interface have been successfully performed.
Web: https://boxybsd.com
Thanks to @gyptazy for this :)
#BoxyBSD #BSD #BSDHosting #Runbsd #vps #freevps #vpshosting #community #education
This lunchtime I have mostly been doing battle with a scsi2sd device, and trying to get my microvax to boot from it as a CDROM.
It's a useful device, but the GUI was obviously put together by the same person who designed and knew the hardware inside out, and the documentation is almost non-existent. It doesn't help that the microvax 3100 is *very* picky about the CDROM drives it will boot from.
I have more #NetBSD than #FreeBSD installs by @rubenerd
https://rubenerd.com/i-have-more-netbsd-than-freebsd-installs/
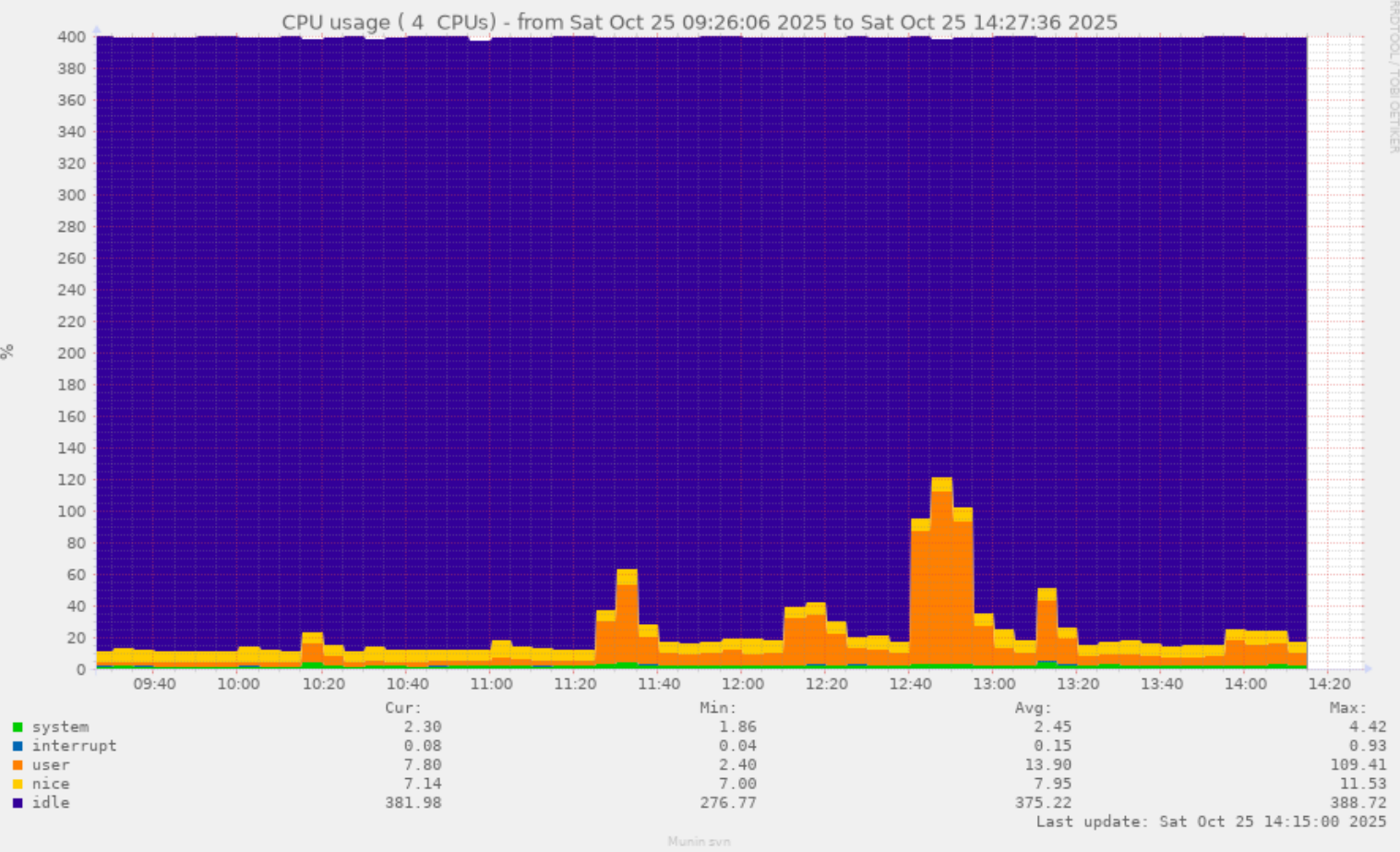
Because I like torturing my Pentium Pro, I'm mentioning this one here. Just in case it should be of interest to anyone. Beware of the slightly nsfw second post in the thread. It's late, my boss is visiting, I had a few beers. It seemed like a good idea at the time. ;)





![[?]](https://weirdr.net/snac/ltning/s/271784d3d55493d08c915e5bb7862aaf.jpeg)


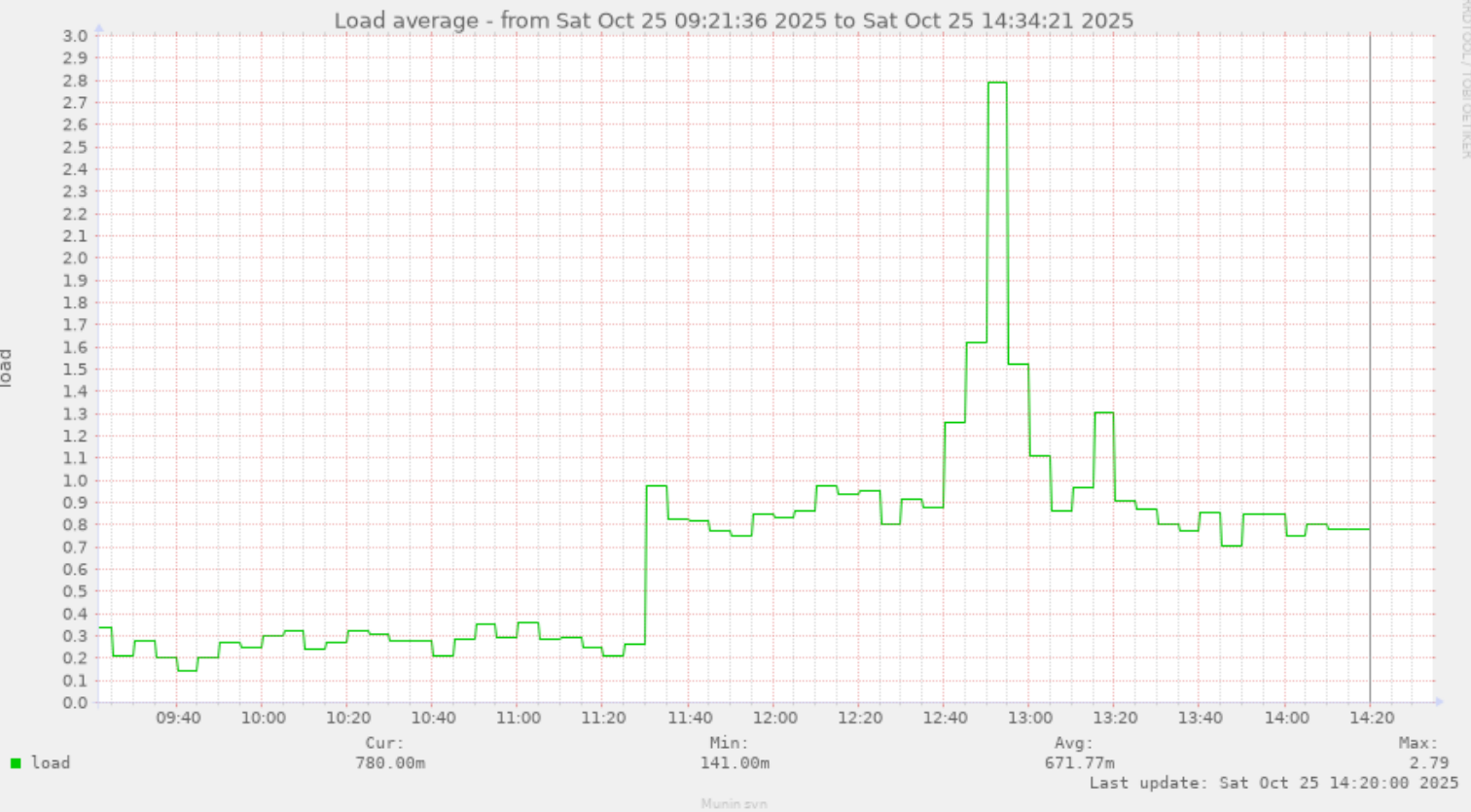
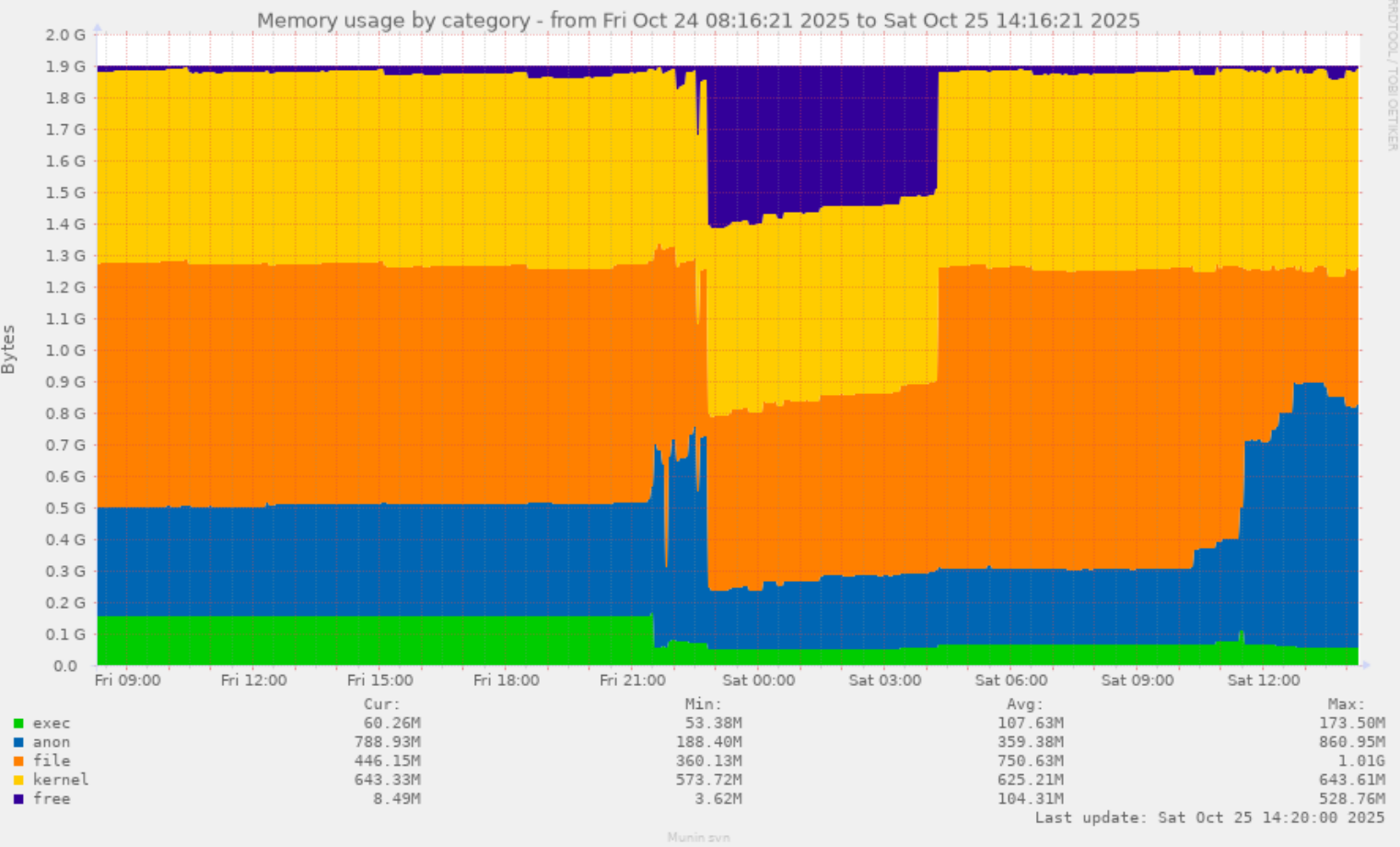
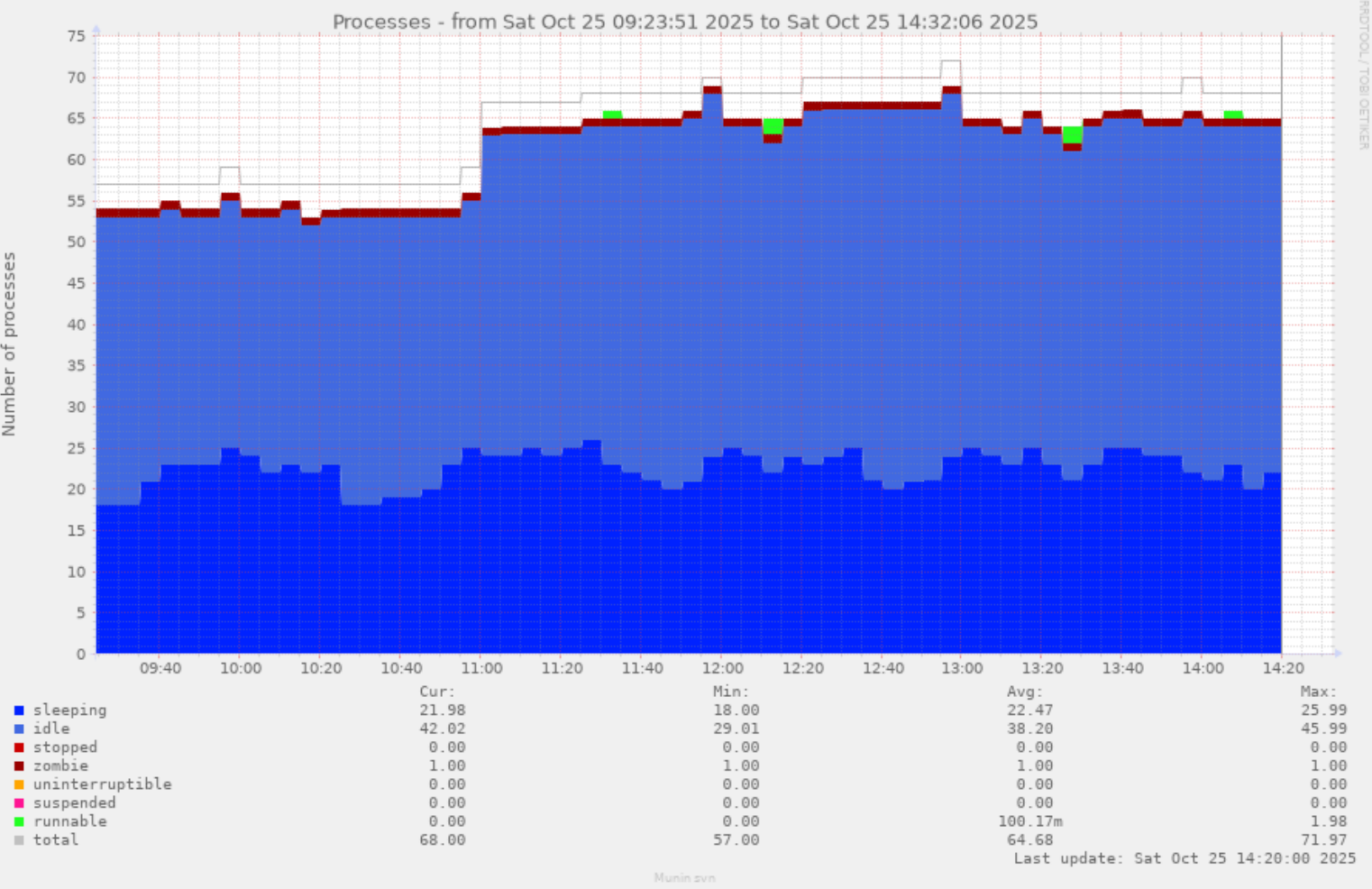
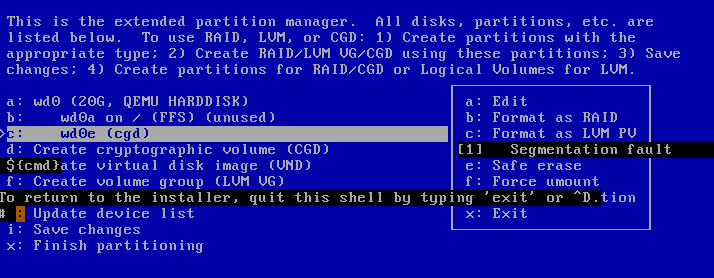



![[?]](https://pleroma.anduin.net/media/e42775318fd38a77b2c02300192e27e61861443424849feef9767918512fac8b.png?name=blob.png)